On Malicious script C:\divtools\word\Word.nec
Alan J. McFarlane
20th November 2003 First version
22nd January 2005 Minor updates [b]
Introduction
A friend with a Packard Bell PC was no longer able to use Microsoft Word after enabling Norton Anti-Virus on the machine. This document contains information on how to fix Word after this occurs, and details of why this behaviour occurs.
What went wrong
On this Packard Bell (/NEC?) PC with Windows XP Home both Microsoft Word and Norton Anti-Virus (NAV) were supplied. When NAV was enabled and Word was run NAV detected “Malicious script detected”. The user decided to ‘Quarantine’ the file, this however stopped Word from working. Below are three methods to fix this. Fix B is probably the best solution if you are experiencing this problem.
Fix A
If you’ve not already Quarantined the script file, then don’t do so! Allow it to run (option “Authorize this script”). Or do Fix B…
Fix B (Recommended)
As described below the “Microsoft Word” start menu item actually points to a script which then starts Word. The script only provides help for the first time Word is run and can be bypassed later. So, one option (and probably the best one) is to re-configure the menu item shortcut to point directly at the Word application file. To do this right-click on the menu item, this will show the Shortcut dialog shown below.
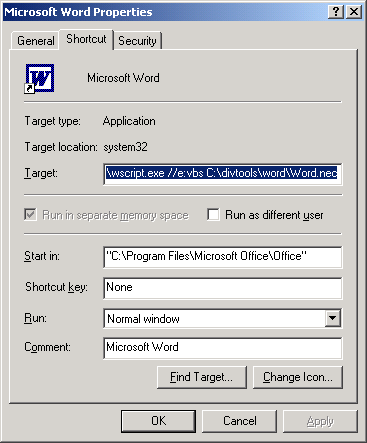
Change the “Target” field to, “winword” and hit OK.
Note, on re-opening, it will contain the value, “C:\Program Files\Microsoft Office\Office\WINWORD.EXE”.
Fix C
This involves restoring the script file from Norton’s Quarantine. The Quarantine feature can be accessed from the NAV Reports screen. Select the “…\word\Word.nec” file and ‘restore’ it.
For complete safety however, you should check that the restored script is as provided originally and has not been infected by a virus subsequently. For instance, check that it looks like the one shown below.
How Word is configured on such machines
The “Microsoft Word” menu option (in the “Home Affairs” folder), rather than running Word directly calls a Windows Script Host (WScript) script that then runs Word. The menu item shortcut thus has the following “Target” value:
C:\WINNT\system32\wscript.exe //e:vbs C:\divtools\word\Word.nec
The purpose of the script is to provide help information to the user; the information tells the user where to find the “product key” that is required to enable Word the first time it is run. The content of the script is:
'on error resume next
Set WShell = WScript.CreateObject("WScript.Shell")
set fs=createobject("scripting.filesystemobject")
Set arg= WScript.Arguments
'création de la clé
Chemin_WORD ="HKEY_LOCAL_MACHINE\SOFTWARE\WORD\"
message="Before using Microsoft Word for the first time you will need to enter the product key. As opposed to what is mentioned on one of the screens that will follow, this product key can be found on the front cover of the Microsoft Word 2000 booklet. Please have this booklet in front of you before continuing."
Variable = Wshell.regread (chemin_word)
if Variable ="0" then
WShell.RegWrite Chemin_word, "1"
rep = msgbox (message,0,"MS Word")
end if
file="C:\Program Files\Microsoft Office\Office\WINWORD.EXE"
if fs.fileexists(file)=true then
WShell.run "winword.exe",1,TRUE
end if
Why
Questions outstanding include: why does Packard Bell supply its machines such that they will detect a virus within their normal configuration? They supply the script and they supply Norton Anti-Virus that detects it as malicious. Not too user-friendly!
References
This situation is described, and Fix B given, on Packard Bell UK’s support site as “Why does Norton AntiVirus 2002 generate the error message "Alert : Malicious script detected"?” at http://support.packardbell.co.uk/pri/index.php?PibItemNr=topic_01534 and as “Note To Customer: Malicious Script Norton AntiVirus - UK” at http://support.packardbell.co.uk/pri/index.php?PibItemNr=6846160101&Ctype=man both from http://support.packardbell.co.uk/pri/index.php?PibItemNr=platform_Falcon.
Note, sadly neither of those articles is found when doing a search on the obvious search term “word.nec” or “word.word.nec”. One has to search on other terms to find them; this document of course will help. :-)
Copyright © 2003-2005 Alan J. McFarlane